- Message digests in java are cryptographic tools used to compute a unique checksum or hash for a specific message.
- Unlike simple checksums such as CRC (Cyclic Redundancy Check), message digests display a critical characteristic.
- Even a minor change in the input can result in a significantly different output hash value.
- The unpredictability of resulting hash values makes it challenging to predict or guess the hash value based on the input message alone.
Message digest example in java
package tutcoach;
import org.bouncycastle.jce.provider.BouncyCastleProvider;
import org.bouncycastle.util.Strings;
import org.bouncycastle.util.encoders.Hex;
import java.security.MessageDigest;
import java.security.NoSuchAlgorithmException;
import java.security.NoSuchProviderException;
import java.security.Security;
public class MessageDigestExample
{
public static void main(String[] args)
throws Exception
{
Security.addProvider(new BouncyCastleProvider());
System.out.println(
Hex.toHexString(
calculateDigest("SHA-256", Strings.toByteArray("Hello World!"))));
}
public static byte[] calculateDigest(String digestName, byte[] data)
throws NoSuchProviderException, NoSuchAlgorithmException
{
MessageDigest digest = MessageDigest.getInstance(digestName, "BC");
digest.update(data);
return digest.digest();
}
}
Output
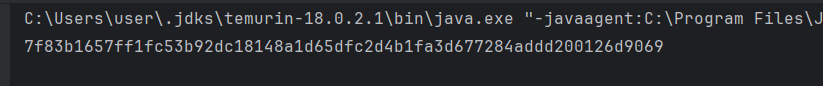
The code snippet showcases a simple example of using a cryptographic MessageDigest in Java.
In the main method of the DigestExample class, a SHA-256 hash is computed for the input string “Hello World!” using the computeDigest method from the JcaUtils class (not shown in the provided snippet). The computed hash is then converted to a hexadecimal representation using Hex.toHexString and printed to the console.
This example illustrates the straightforward usage of a MessageDigest for generating hash values, highlighting the importance of cryptographic techniques in ensuring data integrity and security.
