In the realm of computer security, Java Sandbox Security plays a crucial role by providing a mechanism for isolating running programs to minimize system failures and prevent software vulnerabilities from spreading. Essentially, a Java Sandbox Security is an isolated computing environment where a program or file can execute without affecting the host application. This article delves into the concept, benefits, working mechanisms, and practical implementation of sandboxing in Java.
1. Introduction to Java Sandbox Security
1.1 What is Java Sandbox Security?
Java Sandbox Security is a security mechanism that separates running programs to minimize system failures and prevent software vulnerabilities from spreading. It provides an isolated environment where programs can execute safely without affecting the host system.
1.2 Why Use a Sandbox?
1.2.1 Security
Sandboxing mitigates the risk of malicious code compromising the system by isolating untrusted code from critical system resources.
1.2.2 Isolation
It isolates untrusted code from the rest of the system, reducing potential damage from malicious or faulty software.
1.2.3 Testing
Sandboxes are useful for testing untrusted code or third-party libraries without risking the host environment.
2. How Sandboxing Works in Java
2.1 Java’s Sandbox Model
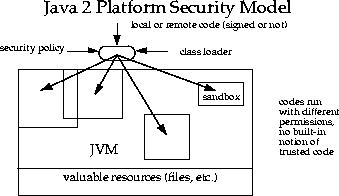
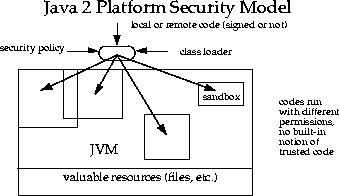
In Java, the sandbox refers to a controlled program area with specific rules that programmers must adhere to when creating Java code, particularly applets embedded in web pages. The sandbox imposes restrictions on what resources the applet can access, similar to children playing within set limits.
2.2 Origins of Java Sandbox Model
Java’s original security model, known as the sandbox model, was designed to provide a highly restricted environment for running untrusted code obtained from the open network, such as applets in web browsers. Local code is trusted with full access to system resources, while remote code (like applets) is confined within the limited resources of the sandbox.
3. Java’s Security Mechanisms
3.1 Language Features
Java’s type safety, ease of use, automatic memory management, garbage collection, and array/string range checking contribute to code safety and reduce programming errors.
3.2 Bytecode Verification
Compilers and bytecode verifiers ensure only legitimate Java bytecodes are executed, enhancing language safety at runtime.
3.3 Classloader Isolation
Classloaders define local namespaces, preventing untrusted applets from interfering with other programs.
3.4 SecurityManager
The SecurityManager class, part of the Java Virtual Machine, restricts untrusted code’s actions to the minimum necessary, ensuring access to vital system resources is controlled.
4. Java’s Approach to Sandboxing
4.1 Security Manager
Controls access to system resources based on a security policy.
4.2 Permissions
Defines what actions code can perform (e.g., read/write files, access network).
4.3 Policy Files
Configuration files that specify the allowed permissions for code sources.
5. Example: Setting Up a Sandbox Environment
5.1 Step 1: Define the Untrusted Code
Create a Java class representing the untrusted code. For this example, let’s create a simple class UntrustedCode.java that prints a message:
public class UntrustedCode {
public static void main(String[] args) {
System.out.println("This is untrusted code running in the sandbox!");
}
}
5.2 Step 2: Create the Sandbox Runner
Create a Java program that sets up the sandbox environment, loads the untrusted code, and executes it within the sandbox:
import java.lang.reflect.Method;
import java.net.URL;
import java.net.URLClassLoader;
import java.io.File;
public class SandboxRunner {
public static void main(String[] args) {
// Set the Security Manager
System.setSecurityManager(new SecurityManager());
try {
// Create a new class loader with the parent set to null (isolated class loading)
ClassLoader loader = new URLClassLoader(new URL[] { new File("untrusted-code.jar").toURI().toURL() }, null);
// Load the UntrustedCode class using the custom class loader
Class<?> untrustedClass = loader.loadClass("UntrustedCode");
// Create an instance of the UntrustedCode class
Object untrustedObject = untrustedClass.getDeclaredConstructor().newInstance();
// Execute the main method of the UntrustedCode class
Method mainMethod = untrustedClass.getMethod("main", String[].class);
mainMethod.invoke(untrustedObject, (Object) new String[0]);
} catch (Exception e) {
System.err.println("Error running untrusted code: " + e.getMessage());
}
}
}
5.3 Step 3: Compile the Code
Compile both UntrustedCode.java and SandboxRunner.java:
javac UntrustedCode.java SandboxRunner.java
5.4 Step 4: Run the Sandbox Runner
Assuming you have compiled UntrustedCode.java into a class file and placed it in a JAR named untrusted-code.jar, run the Sandbox Runner:
java SandboxRunner
The Sandbox Runner will attempt to execute the UntrustedCode class within the sandbox environment. In this example, the untrusted code simply prints a message, but you can replace it with any code that you want to run in the sandboxed environment.
6. Levels of Java Sandboxes
Java’s sandbox model operates on multiple levels of access control, ensuring that programs are confined within specific boundaries based on trust levels and resource requirements. Let’s explore these levels further:
6.1 Minimal Sandbox
Provides access to essential resources like CPU, memory, screen, keyboard, and mouse. This level contains the bare minimum resources necessary for a program to function.
6.2 Default Sandbox
Includes access to the CPU, memory, and the web server from which the program was loaded. Represents the typical state of the sandbox, offering a balanced level of access for most applications.
6.3 Program-Specific Sandbox
Extends access to the CPU, memory, web server, and includes program-specific resources. For instance, a word-processing program may have access to its documents directory but not to other files or sensitive system areas.
6.4 Open Sandbox
Grants access to all resources available to the host machine. This level is less restricted and is usually reserved for trusted applications or environments where full access is necessary.
7. Pros and Cons of Java Sandboxing
7.1 Pros
7.1.1 Security
Protects the system from malicious code by restricting untrusted code’s access to system resources.
7.1.2 Isolation
Prevents unauthorized access to resources, ensuring that untrusted code runs in a controlled environment.
7.1.3 Flexibility
Allows dynamic permission management, enabling fine-grained control over what actions untrusted code can perform.
7.2 Cons
7.2.1 Complexity
Setting up and managing sandbox environments can be complex and requires a deep understanding of Java’s security model.
7.2.2 Performance Overhead
Enforcing security measures may introduce performance overhead, potentially slowing down application execution.
7.2.3 Dependence on Policies
The effectiveness of sandboxing relies on well-defined security policies, which must be regularly reviewed and updated to adapt to evolving threats.
8. Best Practices and Tips for Using Sandbox
- Regularly review and update security policies to adapt to evolving threats.
- Use code signing and trusted code sources to enhance security.
- Monitor sandboxed applications for unusual behavior or security breaches.
- Ensure minimal permissions are granted to untrusted code, adhering to the principle of least privilege.
Conclusion
Java’s sandbox model and associated security mechanisms provide a robust framework for running untrusted code securely. By leveraging features such as the Security Manager, class loaders, and permissions, developers can create isolated environments that safeguard against potential threats while allowing controlled execution. Understanding and implementing these techniques ensures that your Java applications remain secure and resilient in the face of malicious or faulty code.