In this tutorial you will learn asymmetric key cryptography also known as public key cryptography, types of asymmetric key cryptography, advantage and disadvantage of asymmetric key cryptography and current problem in Asymmetric Key Cryptography:
- Asymmetric key cryptography is also known as public key cryptography, is a cryptographic method that uses pairs of keys (public key and private key) for encryption and decryption.
- Each entity has a public key that can be freely distributed and a corresponding private key that is kept secret.
- The public key is used for encryption, while the private key is used for decryption.
- This approach addresses the key distribution problem faced in symmetric cryptography, where both parties need to share a secret key securely.
Asymmetric encryption algorithms
Following are the list of Asymmetric encryption algorithms in public key cryptography.
RSA (Rivest-Shamir-Adleman)
- RSA is based on the mathematical difficulty of factoring large prime numbers.
- RSA is widely used in digital signatures, encryption, and key exchange protocols like SSL/TLS.
- See Rsa encryption and decryption video tutorial
ECC (Elliptic Curve Cryptography)
- ECC (Elliptic Curve Cryptography) cryptography algorithm use the algebraic structure of elliptic curves over finite fields, offering strong security with shorter key lengths compared to RSA.
- ECC is suitable for resource-constrained environments.
DSA (Digital Signature Algorithm)
- DSA cryptographic algorithm is primarily used for generating digital signatures.
- DSA relies on the discrete logarithm problem for security. It’s commonly used in digital certificates and authentication protocols.
Diffie-Hellman Key Exchange
- Diffie-Hellman Key Exchange by itself is not an encryption algorithm.
- Diffie-Hellman allows two parties to establish a shared secret key over an insecure communication channel.
- Diffie-Hellman Key Exchange algorithm is a fundamental component in secure communication protocols like TLS/SSL
How does asymmetric encryption work?
The working process of asymmetric encryption also known as public key cryptography can be divided into different phases starting from key generation phase, encryption phase, data transmission phase, decryption phase, and key storage phase.
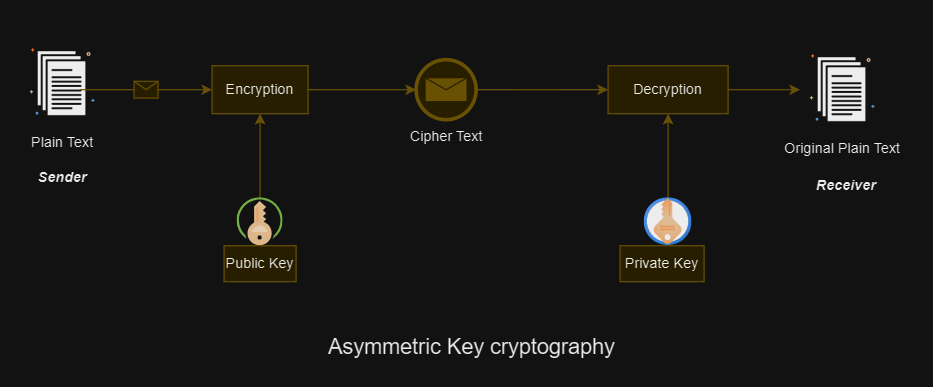
- Key Generation process
- Each entity generates a pair of keys called a public key and a private key.
- The public key is shared openly and can be accessed by anyone.
- The private key is kept secret and known only to its owner.
- Encryption Process
- When Sender wants to send a message to receiver, Sender A obtains receiver public key.
- Sender uses receiver public key to encrypt the message.
- Receiver use his/her private key to decrypt and read the message.
- Decryption Process
- Receiver receives the encrypted message from Sender.
- Receiver uses its private key to decrypt the message and recover the original plaintext message.
- Since the private key is known only to receiver, the message remains confidential.
- Key Usage
- The public key is used for encryption, allowing anyone to encrypt messages intended for the owner of the private key.
- The private key is used for decryption, ensuring that only the owner of the private key can access the decrypted information.
- Security Properties
- Asymmetric encryption provides security through the mathematical relationship between the public and private keys.
- It ensures confidentiality of data as only the intended recipient possessing the private key can decrypt the message.
- It enables digital signatures, allowing entities to verify the authenticity and integrity of messages.
Advantages of Asymmetric Key Cryptography
- Enhanced security
- In Asymmetric key cryptography public keys can be freely shared without compromising the security of the private key.
- Key distribution simplicity
- Asymmetric key cryptography eliminates the need for secure key exchange mechanisms used in symmetric cryptography.
- Digital signatures
- Asymmetric key cryptography enables secure authentication and non-repudiation through digital signatures.
- Versatility
- Asymmetric key cryptography supports a wide range of cryptographic operations, including encryption, decryption, digital signatures, and key exchange.
Disadvantages of Asymmetric Key Cryptography
- Computational overhead
- Asymmetric key algorithms are generally slower than symmetric algorithms, especially for large data sets.
- Key size management
- In public key cryptography long key sizes are required for comparable security which lead to a increased storage and processing requirements.
- Vulnerability to quantum attacks
- Asymmetric algorithms like RSA and ECC are susceptible to quantum computing attacks due to this it might be a necessary for the adoption of quantum-resistant algorithms.
Current Problems in Asymmetric Key Cryptography
- Quantum computing threats
- The advent of quantum computing presents a significant challenge to public key cryptographic algorithms which may lead to the creation of quantum-resistant cryptographic methods.
- Key management challenges
- Managing a large number of public-private key pairs securely can be daunting task, as it requires a robust key management practices and infrastructure.
- Performance considerations
- Balancing security requirements with performance considerations remains a challenge for network professionals where there is a resource-constrained environments such as IoT devices and mobile applications.
Difference between symmetric encryption vs asymmetric encryption
| Aspect | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Key Generation | Uses a single secret key shared between communicating parties. | Uses a pair of keys which are public key and private key. |
| Key Management | Requires efficient key distribution and storage mechanism. | Simplifies key management with public and private keys. |
| Computational Complexity | Generally faster and less computationally complex. | Slower due to key pairs and mathematical operations. |
| Security | Symmetric encryption has strong security but requires secure key sharing mechanism. | Secure key distribution with public keys. |
| Applications | Suitable for bulk data encryption and speed. | Ideal for secure communication and digital signatures. |
| Examples | AES (Advanced Encryption Standard), DES, 3DES. | RSA, ECC, Diffie-Hellman, DSA |
